A Production-Grade Guide for Secure, High-Availability VPN Design in Kubernetes Environments
Kubernetes workloads often need secure, reliable connectivity to external networks: legacy data centers, B2B partners, SaaS services, or multi-cloud environments.
For example, in a fintech company, secure VPN connections may be used to bridge cloud-native payment microservices in EKS with on-prem mainframe systems. Similarly, hybrid cloud migrations often require a VPN layer to enable seamless communication between legacy infrastructure and Kubernetes-based modern applications. Architecting VPN connections within Kubernetes clusters ensures secure, encrypted communication for these use cases.
This blog provides a deep-dive into building High Availability (HA) and Secure VPN architectures in Kubernetes, tailored for production-grade environments and regulatory compliance. to external networks: legacy data centers, B2B partners, SaaS services, or multi-cloud environments. Architecting VPN connections within Kubernetes clusters ensures secure, encrypted communication for these use cases.
This blog provides a deep-dive into building High Availability (HA) and Secure VPN architectures in Kubernetes, tailored for production-grade environments and regulatory compliance.
Why VPN in Kubernetes?
Hybrid Connectivity: Bridge on-prem to Kubernetes for data replication, backups, or legacy system access.
Secure B2B Channels: Protect API integrations and financial transactions.
Multi-Cloud Communication: Connect clusters in AWS, GCP, Azure securely.
Compliance Needs: Meet PCI-DSS, HIPAA, and RBI mandates for data in transit.
VPN vs Alternatives
Use Case | VPN | VPC Peering | Service Mesh |
|---|---|---|---|
Hybrid Cloud | ✅ | ❌ | ❌ |
Secure B2B Comms | ✅ | ❌ | ❌ |
Intra-cluster TLS | ❌ | ❌ | ✅ |
Multi-region K8s | ✅ | ❌ | Partial |
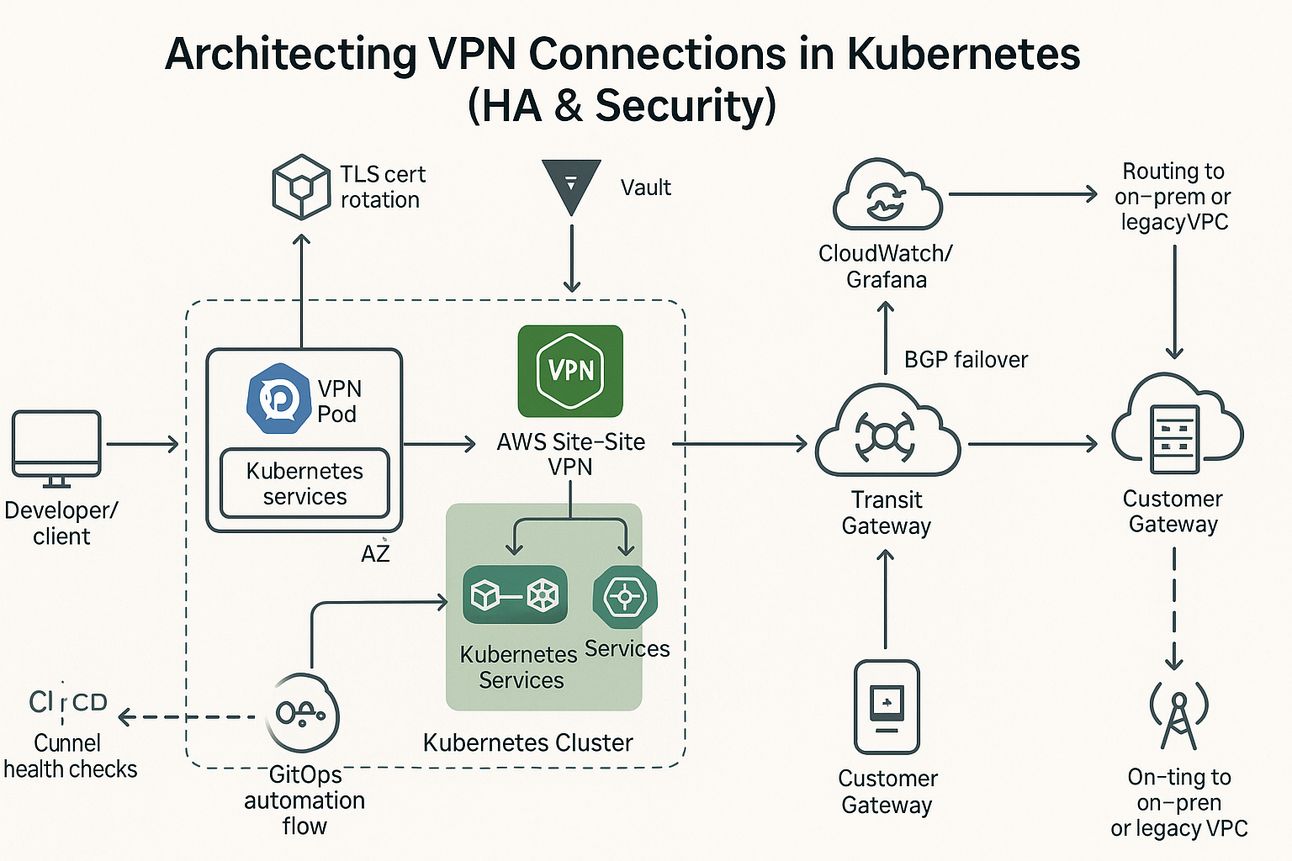
Architecture Patterns
1. Self-Hosted VPN in Kubernetes
Tools: StrongSwan, WireGuard, OpenVPN, AlgoVPN
Deployment patterns:
DaemonSet for node-level tunneling
StatefulSet for HA + identity persistence
Leader election for active/passive IPsec routing
Real-World VPN Setup Snippet (Self-Hosted StrongSwan)
# Install StrongSwan on a self-hosted node
sudo apt update && sudo apt install strongswan -y
# Check IPsec status
ipsec statusall2. Cloud-Native VPN (AWS/GCP/Azure)
AWS Site-to-Site VPN or Transit Gateway + Customer Gateway
Elastic IP to VPN Pod routing
BGP for route propagation
3. Hybrid Model
Cloud-native VPN termination → Forward traffic to VPN Pods within the cluster
High Availability (HA) Design
Active/Active Tunnels across AZs
HA via BGP Failover in StrongSwan
Use of readiness/liveness probes to detect tunnel failure
Elastic IPs or AWS NLB for consistent endpoint access

Security Best Practices
Example: cert-manager ClusterIssuer for VPN TLS
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: vpn-issuer
spec:
acme:
server: https://acme-v02.api.letsencrypt.org/directory
email: [email protected]
privateKeySecretRef:
name: vpn-issuer-key
solvers:
- http01:
ingress:
class: nginxTLS Certificates with automated rotation via cert-manager. Set up cert-manager using its Helm chart or YAML manifests, and configure an Issuer (or ClusterIssuer) to automatically manage TLS certificates for your VPN services. Leverage annotations in your VPN Pod services or Ingress objects to bind certificate generation and renewal seamlessly.
For detailed implementation, refer to the official guide: https://cert-manager.io/docs/. via cert-manager
Secrets managed via Kubernetes Secrets, Sealed Secrets, or Vault
NetworkPolicies to scope traffic only to/from VPN Pods
Firewall rules at the VPC level to restrict ingress
eBPF observability for VPN interfaces (Cilium/BCC)
Traffic Routing & DNS Management
Split Tunnel vs Full Tunnel routing in VPN Pods
iptables/NAT inside pods to redirect to tun0
DNS: CoreDNS customization for .corp or .b2b zones
DNS Leak Prevention via encrypted DNS over VPN
ExternalDomains plugin or kube-dns forwarding for hybrid setups
Inter-Cluster VPN Communication
VPN between clusters in EKS (Mumbai) and GKE (Singapore)
Use of Submariner or StrongSwan for cross-cluster encrypted routing
Shared CIDR ranges and Kubernetes
EndpointSlicesyncMulti-cloud K8s DR replication via VPN
Multi-Tenant Cluster Considerations
Isolated Namespaces with scoped VPN access
NetworkPolicies per tenant
ResourceQuota to control VPN bandwidth hogging
Namespace-scoped Sidecar VPN model for tenant-specific tunnels
ServiceAccount IAM role mapping for scoped VPN permissions
Disaster Recovery & Chaos Testing
CI/CD Pipeline Health Check (Tunnel Validity)
# Run inside a CI pipeline or Kubernetes Job
curl -s --connect-timeout 5 --interface tun0 https://secure-b2b-api.example.com || echo "VPN tunnel might be down"Simulate VPN outage using Chaos Mesh or AWS FIS
Validate HA failover by terminating primary tunnel
CI/CD pipelines with synthetic traffic + tunnel health probes
Slack/Webhook alert on VPN tunnel downtime
Include VPN tests in GameDay DR Drills
Performance Tuning & Optimization
MTU tuning: Prevent packet fragmentation inside VPN (1400–1420 bytes optimal)
sysctltuning on nodes:net.core.rmem_max,net.ipv4.tcp_mtu_probingCPU/mem resource requests for encryption-heavy VPN Pods
WireGuard for high-speed/low-latency VPN setups
IAM & Access Control
Map OpenVPN users to Kubernetes RBAC using LDAP/SAML
Auto-expiring keys with
kubectl cert-manager renewConditional IAM roles for VPN access per environment (dev/stage/prod)
Vault-based dynamic certs for just-in-time VPN access
Observability & Monitoring
Prometheus exporters:
openvpn_exporter,strongswan_exporterFluentBit/Vector log shipping for VPN logs
Grafana dashboards for:
Tunnel latency
Active sessions
Disconnect events
AWS CloudWatch alarms for VPN Tunnel Down status
Alertmanager integration with Opsgenie/Slack
openvpn_exporter,strongswan_exporterFluentBit/Vector log shipping for VPN logs
Grafana dashboards for:
Tunnel latency
Active sessions
Disconnect events
AWS CloudWatch alarms for VPN Tunnel Down status
Alertmanager integration with Opsgenie/Slack
Cost Optimization
Terraform Snippet: AWS VPN + Customer Gateway
resource "aws_customer_gateway" "example" {
bgp_asn = 65000
ip_address = "203.0.113.12"
type = "ipsec.1"
}
resource "aws_vpn_connection" "vpn" {
customer_gateway_id = aws_customer_gateway.example.id
type = "ipsec.1"
vpn_gateway_id = aws_vpn_gateway.example.id
}Compare AWS VPN Gateway vs WireGuard on Spot Nodes:
VPN Option | Type | Approximate Cost (Monthly) | Notes |
|---|---|---|---|
AWS VPN Gateway | Managed | $36 per VPN connection | Highly available, easy setup |
StrongSwan on EC2 | Self-Hosted | ~$15 on t3.small instance | Full control, requires maintenance |
WireGuard on Spot | Self-Hosted | ~$5–10 on spot t3.micro | Cost-efficient, ideal for test/dev |
NAT Gateway (for VPN) | AWS Managed | ~$32.40 per AZ | Charges per GB and hour |
Static EIP + Routing | AWS Native | Minimal | Requires NAT setup via EC2 or custom Pod |
Use spot-tolerant DaemonSets with anti-affinity
Shared VPN Pod per tenant when usage is low
Use of lightweight Alpine images with built-in VPN binaries
Refer to AWS pricing page for exact costs: https://aws.amazon.com/vpn/pricing/ on Spot Nodes
NAT Gateway vs Static IP with Egress-only routing
Use spot-tolerant DaemonSets with anti-affinity
Shared VPN Pod per tenant when usage is low
Use of lightweight Alpine images with built-in VPN binaries
Compliance & Regulatory Readiness
PCI-DSS: Encryption standards (AES-256), Key rotation
HIPAA: BAA-compliant cloud-native VPN (AWS)
RBI: VPN + PrivateLink/Transit Gateway for Indian banks
Audit logging of VPN access attempts
Automated CIS Benchmark checks on VPN Pods
Tool Comparison Table
Tool | Type | Strength | When to Use |
|---|---|---|---|
StrongSwan | Self-Hosted | IPsec + HA | Site-to-Site, regulated workloads |
WireGuard | Self-Hosted | High-speed | Low-latency, fast encryption |
OpenVPN | Self-Hosted | SSL-based | Client access, legacy systems |
AWS VPN Gateway | Managed | Easy HA | Hybrid cloud, production DR |
AlgoVPN | Automated | Lightweight | Quick deploy VPN for dev/test |
Submariner | Multi-Cluster | Encrypted cluster comms | Multi-K8s DR |
Lessons Learned
Treat VPN in Kubernetes as a critical production component — not a one-off config.
Design for HA from the start: active/active tunnels, BGP failover, zone-aware deployment.
Secure everything: TLS certs, access scopes, DNS hygiene, secrets encryption.
Monitor aggressively: latency, tunnel drops, disconnections, resource limits.
Automate consistently: Terraform, Helm, GitOps pipelines.
Conclusion
Architecting secure, HA VPNs in Kubernetes is critical for hybrid cloud, compliance, and production DR use cases. By blending cloud-native services like AWS VPN Gateway with self-hosted options like StrongSwan or WireGuard, you can achieve secure, scalable connectivity. Adding observability, automation, and compliance enforcement makes the architecture production-grade.
Integrating VPN deployment, monitoring, and failover validation into Terraform and GitOps pipelines ensures consistent, auditable, and repeatable operations across environments. This not only reduces human error but also enforces best practices as code.
Avoid the VPN-as-a-script trap — treat it like a critical microservice, backed by automation and observability. is critical for hybrid cloud, compliance, and production DR use cases. By blending cloud-native services like AWS VPN Gateway with self-hosted options like StrongSwan or WireGuard, you can achieve secure, scalable connectivity. Adding observability, automation, and compliance enforcement makes the architecture production-grade.
Avoid the VPN-as-a-script trap — treat it like a critical microservice.